Report DIVD-2022-00014 - Greynoise's Ukraine Only list
Written on 16 Dec 2022 by Gerard Janssen
Case lead:
Frank Breedijk
Case file: DIVD-2022-00014
On February 24, 2022, Andrew Morris – founder of cyber security company GreyNoise Intelligence – tweeted about a “free, public, unauthenticated, self-updating feed of all IPs that are exclusively targeting devices geographically located in Ukraine’s IP space with scans, exploits, etc.”
GreyNoise Intelligence is based in Washington DC and analyzes ‘Internet background noise’, in this case, IP addresses targeting ‘honey pots’ based in Ukraine. The DIVD examined the list with IP addresses and found that some of the IP addresses were compromised NAS servers, routers, and AWS instances.
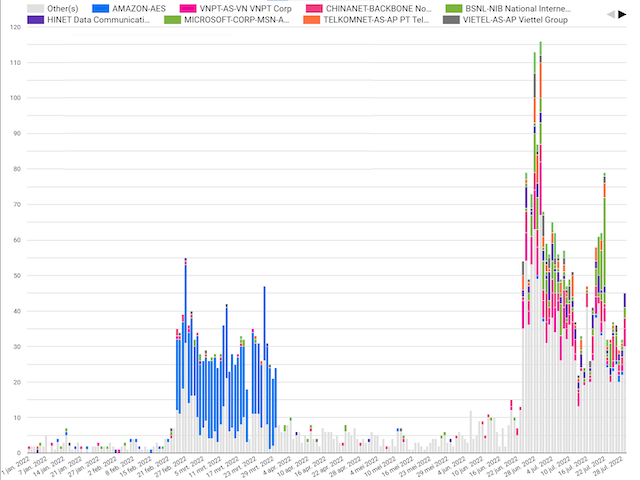
Overall the DIVD sent 5698 notifications to owners of the IP addresses that appeared on the list.
GreyNoise stopped updating the API after 1 Aug 2022 and the DIVD closed this case on August 15, 2022.
This case was unusual Therefore DIVD’s ethical commission evaluated the case on October 5, 2022. TIt ruled that this case falls outside the current Code of Conduct (CoC) version because the attacker is more than likely one threat actor. The DIVD has taken the position not to cooperate (offensively) in global conflicts in which the Netherlands is not directly involved.
Timeline
| Date | Description |
| 24 Feb 2022 | GreyNoise announces their plans to publish a feed of IP’s that target devices geographically located in Ukraine |
| 04 Mar 2022 | Case opened |
| 05 Mar 2022 | First notifications sent |
| 31 Jul 2022 | Last update to Greynoise Ukraine only list |
| 15 Aug 2022 | Case closed |
| 05 Oct 2022 | Verdict ethical commission |